ISO 27001
Certification
Our products empower clients to attain and maintain their ISO 27001 certification through automation, ensuring data confidentiality, integrity, and availability.
CMMC Certified
Our solutions enable clients to enhance their cybersecurity practice, facilitating their journey towards achieving CMMC compliance and ensuring robust protection against cyber threats.
SOC 2 Compliance
Our platform enables clients to implement the highest standards for security, availability, processing integrity, confidentiality, and privacy, thereby simplifying their path to achieving and maintaining SOC 2 compliance.
CIS Controls
Our services leverage the Center for Internet Security (CIS) Controls to help clients mitigate risks and enhance their cybersecurity posture, guiding them towards effective implementation of CIS best practices across their operations.
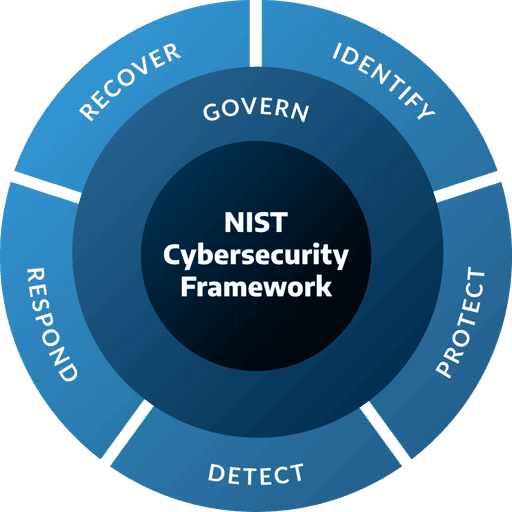
NIST CSF
Our platform allows clients to meet and maintain compliance NIST Cybersecurity Framework (CSF), by identifying, protecting, detecting, responding to, and recovering from cyber threats, thereby enhancing their overall cybersecurity strategy.
NIST 800-53
Our solutions implement security controls based on NIST 800-53, enabling clients to achieve and sustain compliance with rigorous federal-level security and privacy standards, ensuring the protection of their sensitive data.